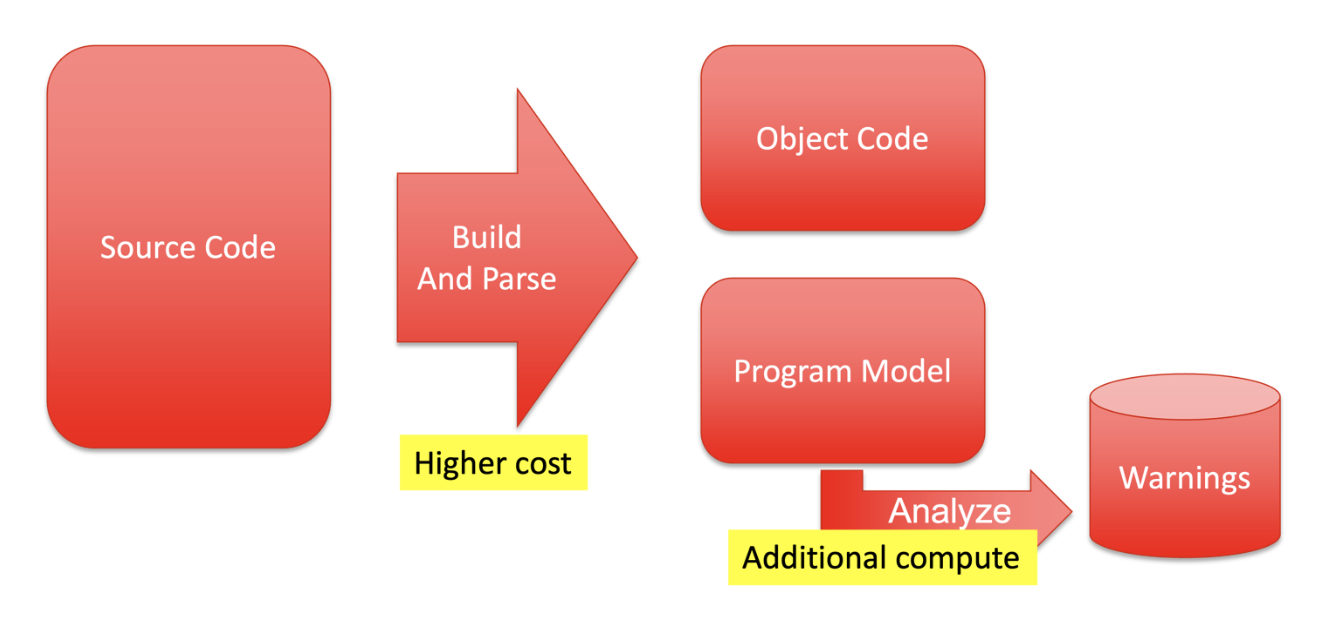
Having an SBOM and software inventory aids in identifying 3rd-party vulnerabilities and risk
Let’s take a quick look at two popular open-source software (OSS) components that were recently flagged regarding new vulnerabilities:
- SQLite – a popular database engine written in the C programming language whose libraries are often embedded in other apps
- OpenSSL – an open-source implementation of the SSL and TLS cryptographic protocols which make secure communications possible (think the lock icon next to your browsers web address)
SQLite 1.0.12
On October 25, the exploitability of SQLite API CVE was published by Trail of Bits. Great analysis is here: https://lnkd.in/ejUKAUcA.
In summary, there is a confirmed vulnerability in SQLite before 3.39.2, on 64 bit systems, where one of the APIs can be exploited to lead to arbitrary code execution when it is compiled with stack canaries off. The vulnerability is not confirmed with stack canaries on.
Know what uses SQLite? Firefox. The up-to-date Firefox version installed on my Windows machine has SQLite version 3.38.3, very new, but still vulnerable based on the CVE info. The library is contained in nss3.dll, which luckily is compiled with stack canaries on.
How do I know? I analyzed the binaries that are installed on my system with GrammaTech CodeSentry. This gave me an SBOM, which confirms the presence of sqlite 3.38.3 and it also gives me a ‘Security Attributes’ report, which indicates that stack canaries are on.
Now, unclear if this vulnerability can be exploited through the inclusion in Firefox, but having a software inventory means I can take quick action if required at a later point in time.
OpenSSL 3.0
On October 27, the OpenSSL project pre-warned that a critical update (OpenSSL 3.0.7) is due to be announced on November 1: https://lnkd.in/eJmsnn_U.
The question then becomes whether or not you have OpenSSL 3.0 in your current software inventory. This is what SBOMs were intended to assist with. If you are one of the lucky few that have SBOMs for the software in your inventory, great! You know where you may be exposed and you can take quick action on November 1st.
If not, then GrammaTech CodeSentry can help to create an SBOM for binary software that you depend on.
I have been scanning some of the applications I use to see where OpenSSL 3.0 is being used and so far the VPN client, screen sharing, videoconferencing and database software I use are all still on OpenSSL version 1.1.1i through 1.1.1o. My blood pressure is slowly going down, but I will continue scanning.
Bottom line – Everyday, Software Supply Chain Security matters!
Read more about GrammaTech’s most up-to-date OpenSSL 3.0 remediation plan and risk assessment here