REAFFIRM: Reverse Engineer and Fuzz Firmware
Unpacking, Analyzing, and Securing Firmware for Cyber-Physical System Protection
REAFFIRM (Reverse Engineer, Analyze and Fuzz Firmware) is a platform for firmware analysis, component identification and extraction, and testing. REAFFIRM facilitates cyber security assessments for cyber-physical systems used in the military (weapons controls, navigation systems), critical infrastructure (industrial-control systems) and everyday applications (automotive controls, medical devices).
To help analysts achieve a deep understanding of firmware, REAFFIRM’s analyses identify meaningful components, present them, and rank them by relevance. This enhanced understanding facilitates both cyber security assessments and evaluations of the firmware for reuse in new settings.
Cyber security testers can use REAFFIRM to extract key components for testing. Because our system identifies, isolates, and virtualizes the hardware-coupled portions of firmware components, testing can proceed in a virtualized environment, without the expense and risk of damage associated with using real hardware.
Through its use of data science tools such as Jupyter notebooks, REAFFIRM supports reproducibility and gradual automation of reverse-engineering and testing workflows.
Need
Firmware vulnerabilities are a significant security concern, with 83% of businesses experiencing a firmware attack in the past two years [Microsoft].
Current cybersecurity solutions address network and software security, through advanced threat detection systems, intrusion prevention systems, and regular security updates. However, few options are available to secure firmware, the embedded software that runs critical systems, leaving a gap in the defense perimeter.
Firmware requires specialized tools for analysis and protection. Source code is seldom available, and testing is difficult as it requires the device hardware.
Solution
REAFFIRM automates the unpacking, disassembly, and analysis of firmware.
- Supports many common firmware architectures such as IA32/X64, ARM, PPC, and MIPS
REAFFIRM provides an end-to-end pipeline from raw binary packages to actionable results:
- Unpacking and extraction prepare available packages, such as vendor firmware updates, and find components to analyze
- Deep static analysis reveals functionality, including potentially unintended design flaws
- Targeted dynamic analysis (fuzzing) on firmware components finds hidden weaknesses
- Multiple interfaces support workflow integration: Jupyter Notebook graphical interface, command-line interface and Python API
Benefits
Reduces time, effort, and expertise for firmware analysis and inspection.
Improves analysis efficiency and automation, for a quicker and more accurate identification of security risks.
Delivers actionable information to security analysts (detected flaws) and reverse engineers (location of relevant code), in a user-friendly environment.
System and Workflow
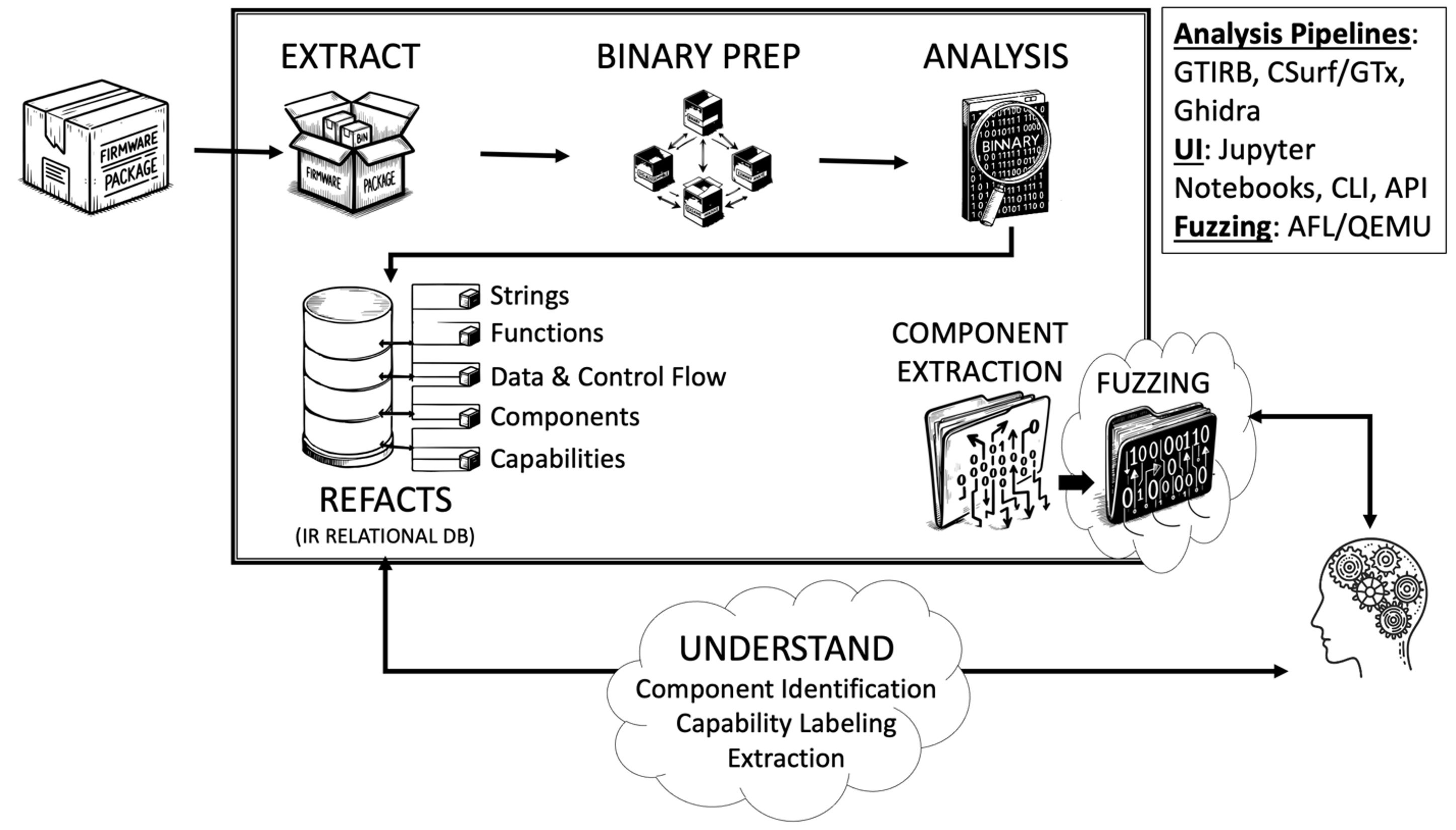
User Interaction: available to query database and interact with analysis, extraction, and fuzzing
Automation: Python API, Command Line, and Jupyter Notebooks to integrate into your workflow
REAFFIRM in Practice C
-
We benchmarked REAFFIRM on a dataset of 20 diverse embedded networking firmware images, used in a recent competitive firmware analysis event.
- REAFFIRM is able to unpack 17/20 images, run system analysis on 15/20, and run binary analysis on 14/20.
- In 2024, a major defense contractor purchased a REAFFIRM license and support, to accelerate reverse engineering of binary firmware.
REAFFRIM for you
- Offered through a flexible licensing and subscription-based model
- Available as both an on-premises and SaaS solution
- If desired, GrammaTech’s firmware analysis experts can perform the reverse engineering work, delivering insights and security evaluations.
References:
[Microsoft] “Security Signals.” (2021, March). Page 24. Microsoft. https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RWPStZ
© 2024 Grammatech, Inc.