
The Common Weakness Enumeration (CWE) Top 25 most dangerous software errors, a.k.a., the CWE Top 25 is a list of the most common weaknesses that lead to security vulnerabilities. It is published on a regular basis by MITRE, as of this post, the most recent coming out in September 2019. The CWE lists are based on data collected from the Common Vulnerabilities and Exposures (CVE) found within NIST National Vulnerability Database (NVD).
Put simply, the CWE Top 25 lists the errors that are the most dangerous based on observed vulnerabilities found in current software products. This is useful information for developers since they can use the list to prioritize what types of software weaknesses to investigate and avoid or fix. Unfortunately, despite these efforts to inform the public, many of the top weaknesses are front-runners year after year.
The Role of Static Analysis
Static analysis plays an important role in detecting these weaknesses in code or to help assess existing code bases (discussed in this post.) We’ve written quite a bit about the role of static analysis in helping software managers and developers in improving security, here’s a quick summary of how advanced static analysis helps improve security beyond just detecting the CWE Top 25:
- Continuous source-code quality and security assurance: As each new code block is written (file or function), it can be scanned by static analysis tools, detecting errors and vulnerabilities (and maintaining secure coding standards, discussed below) in the source before it enters the build system.
- Tainted data detection and analysis: Analysis of the dataflows from sources (i.e. interfaces) to “sinks” (where data gets used in a program) is critical in detecting potential vulnerabilities from tainted data (containing potential exploit payloads).
- Assessing the quality and security of third-party code: Most projects are not greenfield development and require the use of existing code within a company or from a third party. Performing testing and dynamic analysis on a large existing codebase is hugely time consuming and may exceed the limits on the budget and schedule. Static analysis is particularly suited to analyzing large codebases and providing meaningful errors and warnings that indicate both security and quality issues. CodeSonar’s binary analysis can analyze binary-only libraries and provide similar reports as source analysis when source is not available. In addition, binary analysis can work in a mixed source and binary mode to detect errors in the usage of external binary libraries from the source code.
- Secure coding standard enforcement: Static analysis tools analyze source syntax and can be used to enforce coding standards. Various code security guidelines are available such as SEI CERT C and Microsoft’s Secure Coding Guidelines.
In the end, there is always a balance to strike between investing in security and investing in new feature content. Static analysis tools help managers find that balance by automating security and quality testing early in the development cycle. For this it’s key to be able to detect as many of the CWE Top 25 as possible but it’s also important that static analysis tools integrate into a professional development environment and provide a way to manage these detected vulnerabilities efficiently over time.
CodeSonar for Compliance with CWE for Source and Binary Code
CodeSonar’s advanced static analysis engine automatically detects over 100 types of security vulnerabilities in source and binary code which means accurate and efficient elimination of security risks as code is written at the developer’s desktop, as part of a continuous integration and deployment pipeline or as an evaluation project for third party, open source and legacy code.
CodeSonar’s warning classes also support several coding initiatives, including the CWE and SEI CERT C, which is an excellent preventive measure for avoiding the Top 25 and many other security issues down the road. CodeSonar has been certified as CWE-Compatible, recognizing that it supports the CWE to the highest level currently recognized by the organization. The mapping of CodeSonar C/C++ warning classes is provided here and for Java.
Support for the latest list, as of September 2019, is possible by using the following search string settings in the CodeSonar web portal:
(categories:”CWE:119″ OR categories:”CWE:79″ OR categories:”CWE:20″ OR categories:”CWE:200″ OR categories:”CWE:125″ OR categories:”CWE:89″ OR categories:”CWE:416″ OR categories:”CWE:190″ OR categories:”CWE:352″ OR categories:”CWE:22″ OR categories:”CWE:78″ OR categories:”CWE:787″ OR categories:”CWE:287″ OR categories:”CWE:476″ OR categories:”CWE:732″ OR categories:”CWE:74″ OR categories:”CWE:434″ OR categories:”CWE:611″ OR categories:”CWE:94″ OR categories:”CWE:798″ OR categories:”CWE:772″ OR categories:”CWE:400″ OR categories:”CWE:426″ OR categories:”CWE:502″ OR categories:”CWE:269″ OR categories:”CWE:295″ OR categories:”CWE:835″ OR categories:”CWE:522″ OR categories:”CWE:704″ OR categories:”CWE:362″ OR categories:”CWE:918″ OR categories:”CWE:285″ OR categories:”CWE:601″ OR categories:”CWE:415″ OR categories:”CWE:306″ OR categories:”CWE:532″ OR categories:”CWE:384″ OR categories:”CWE:617″ OR categories:”CWE:326″ OR categories:”CWE:427”)
Figure 1: Search settings for the CWE Top 25 plus “On the Cusp” warnings
Using these search settings provides a report on the latest 2019 CWE Top 25 plus the “on the cusp” warnings that are the next 15 most common weaknesses. An example report is shown below, and unsurprisingly the most common weakness found was tainted buffer access (none other than the top of the CWE Top 25 list!)
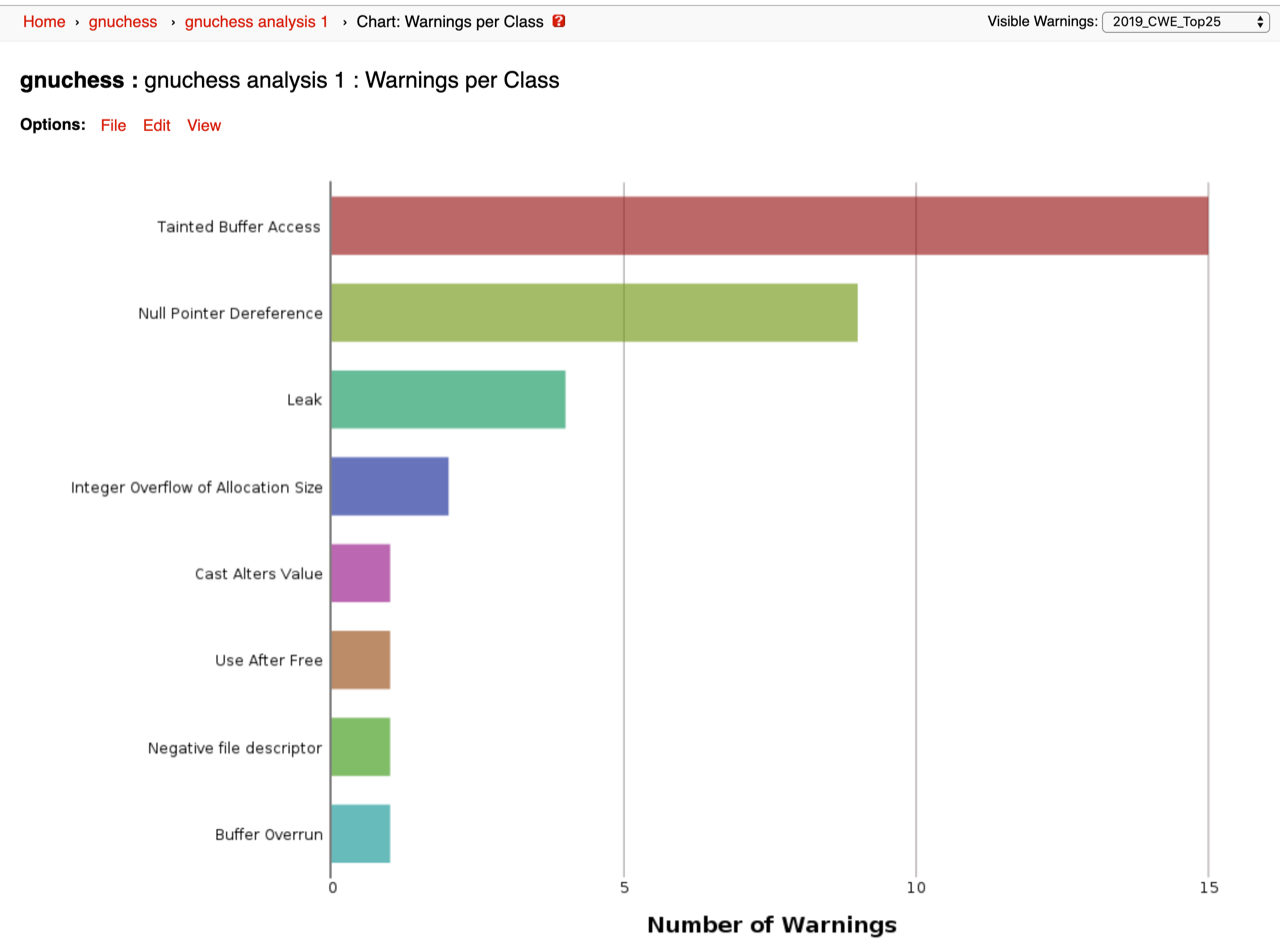
Figure 2: Example report from the CodeSonar web portal
In summary, CodeSonar has a proven track record with finding security vulnerabilities and is certified as CWE compliant. Using the strong search functionality, it’s possible to quickly add new custom reports for the latest (and future) CWE Top 25 updates.