The Government Accounting Office (GAO) was asked to review the state of the Department of Defense (DOD) weapons systems’ cybersecurity. Unfortunately, their findings were not encouraging. The GAO findings included “DOD faces mounting challenges in protecting its weapon systems from increasingly sophisticated cyber threats”, “In operational testing, DOD routinely found mission-critical cyber vulnerabilities in systems that were under development” and “program officials GAO met with believed their systems were secure and discounted some test results as unrealistic.”
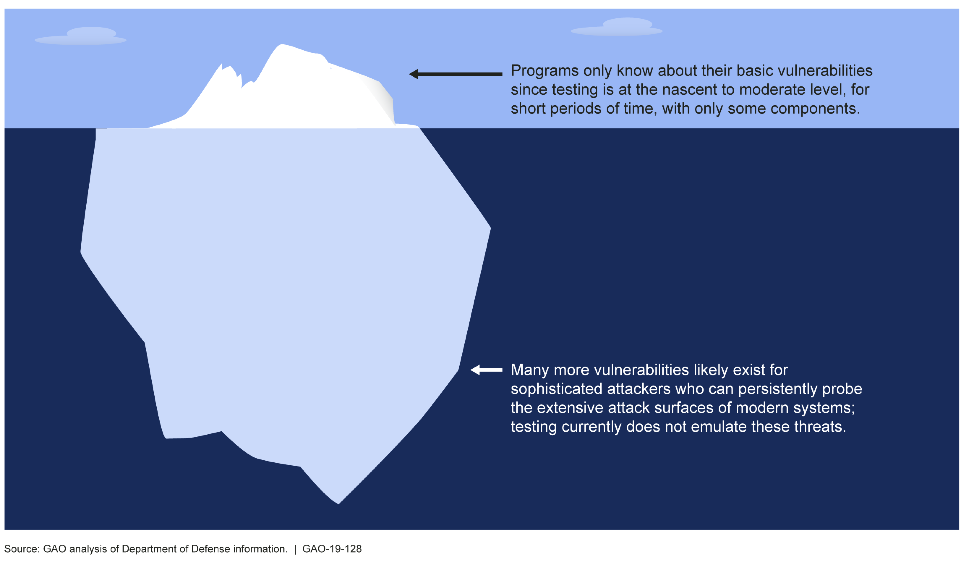
Given the scale of DOD’s acquisition programs ($1.66 trillion) the cybersecurity problem is large and complex. In fact, it’s likely bigger than what is currently known and the GAO’s report illustrates this well with their iceberg diagram, shown below.
What Security Testing Found
According to the GAO report, DOD has been testing various weapon systems’ security. However, this was a limited set of tests and systems. Despite this, their findings are likely indicative of systemic and widespread problem. The GAO found that “testers routinely found mission-critical cyber vulnerabilities in nearly all weapon systems that were under development” and that “using relatively simple tools and techniques, testers were able to take control of these systems and largely operate undetected.” Most of the findings by DOD security testers, as reported by GAO, fall into the “who’s who” of security vulnerabilities:
- Failure to prevent unauthorized access: In many of the systems tested, test teams easily gained basic access almost immediately, gaining full control within a day’s work. Some systems were able to thwart malicious remote access but did nothing to prevent insider and “near-sider” attacks.
- Privilege escalation: Test teams were able to escalate their access privileges in compromised systems easily.
- Poor protection from malformed data: Penetration testing proved problematic for many systems, scanning and “attacking” the system with malformed data. In fact, one test had to be stopped due to safety concerns.
- Poor password management: Some systems showed lack of proper password management, either because of reused defaults or simple-to-guess passwords.
- Insufficient security controls: Tested systems had implemented role based access (a good thing when done properly) but all communication between users was unencrypted, allowing access to usernames and passwords.
- Poor vulnerability management: Reports from previous cybersecurity assessments were ignored or not properly followed up on. Test teams were able to reuse previously reported vulnerabilities to attack systems.
- Poor intrusion detection: Many systems displayed little or no ability to detect malicious behavior or access. Test teams were able to remain undetected for weeks.
- Lack of response and recovery: In many cases, attacks went unnoticed due to lack of detection. In other cases, operators were able to detect an attack but the system lacked a capability to respond.
The testing performed was limited as the teams reporting these vulnerabilities had limited time with each system. This leads to conclusion that many vulnerabilities remain undetected and the problem is severe, a “tip of the iceberg”, as illustrated above.
DOD Response
Weapon systems’ cybersecurity is a well-known issue for DOD and they have taken steps to respond. Since 2014 DOD has issued department wide policies and guidance to help secure weapon systems, including an overall cybersecurity strategy, risk management framework, and test and evaluation guide among others. Probably to key response is to apply security guidelines specifically to weapon systems, IT and network infrastructure was already covered under existing information assurance guidelines.
The first step is to admit there is a problem and this seems to be the case although implementation will be slow. Given this focus on security and the need to respond quickly with critical systems, there lies opportunity. Opportunity for security professionals, vendors and DOD. Let’s consider some of the benefits from a vendor point of view.
The Opportunity
Rather than discussing the commercial opportunity, I’d like to consider the opportunity that exists for vendor in terms of applying and improving solutions, potential areas for research and development and advocacy to prevent such situations in the future.
- Completing the picture: Only the tip of the iceberg is known at the moment and the scale of the problem is still unknown. Software, hardware and security expertise can help expose the problem farther by detecting and documenting a more complete set of vulnerabilities. Admitting the problem is a start but understanding the scale, is next.
- Cleaning up the mess: Although we push for security to be designed-in, it’s often not and many systems go to market unprotected and vulnerable to attack. However, it’s possible to help “stop the bleeding” on current programs underway and to help retrofit systems in place. For example, in areas that GrammaTech specializes, there’s opportunity to apply state of the art software tools to existing software to detect vulnerabilities or contain the problem via runtime detection and prevention. Other opportunities exist in automated security testing and vulnerability management, for example.
- Doing better in the future: Obviously, DOD and GAO have realized a large problem that needs a retroactive response, since systems are almost fully developed or already fielded, guidelines and regulations for new programs should help prevent this in the future. Industry participation in new standards provides input from many sources, points of view and expertise – hopefully advancing the state of the art in the process. All software developers need to take security more seriously and, hopefully, a new era of security-aware development teams curb the problem on future programs. A huge opportunity exists in training as teams seek out security expertise. New development methods, designing-in security, and software tools can help projects take a leap in productivity while improving quality and security.
- Research and development: Recognizing the problems with cybersecurity for new, existing and legacy systems, DARPA has funded research in many related areas, of which GrammaTech is or has participated in. Securing deployed systems at runtime is a key area of research that includes isolating and protecting an insecure system from potential attacks with runtime detection and protection when attacks occur.
Other areas of research include vulnerability detection in binary code to thwart vulnerabilities in firmware, libraries and third party code. Probably GrammaTech’s largest success in this area is our success at the Cyber Grand Challenge sponsored by DARPA. GrammaTech and the University of Virginia’s team, TechX, built an autonomic ‘intelligent’ software runtime environment with self-awareness, monitoring for deviations from expected behavior, assessing mission health, and reacting to preserve the system’s functionality – raising alerts, initiating recovery processes, or shutting the system down in order to protect critical data.
Summary
The GAO report on the state of DOD weapon systems cybersecurity paints a dour picture. Steps are being taken to improve security which should improve security for future programs and potentially some programs in progress. The problem, although huge, presents an opportunity for companies in the security improvement and assurance marketplace for not only business but improve their own processes, tools and techniques. In addition, completed and underway research and development is already making an impact on the problem.